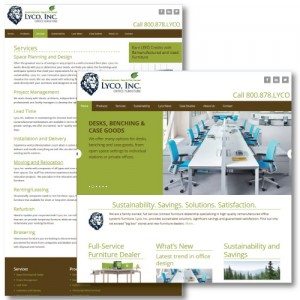
A new updated WordPress website designed for Lyco, Inc., a long time customer of Web Savvy Marketers. We had designed their original website several years ago.
5 Online Marketing No-No’s

Online marketing can be a daunting undertaking, especially when you’re a small business that’s used to traditional advertising. You’re also bound to make mistakes as you try to absorb all the information and apply it to your company.
Stepping out into the internet world of online marketing and knowing what not to do can be helpful. The following five online marketing no-no’s are practices you want to avoid when making the transition from traditional marketing into a successful online marketing plan.
1. No Blog
Not having a blog for your business makes it harder for people to find you. Every time you create valuable content, you’re giving Google and other search engines the cue to index your page, which will show up in search results and drive more traffic to your website.
Because let’s face it, how often do you update the pages of your website? With regular blogging, you are helping more people to discover what you have to offer – not just those who are typing in your business name when searching.
Blogging useful content generates conversation, creates leads, and keeps customers. Give Google something to crawl your website for more often, which will give you better search engine results.
2. No Local Search
Recently, a small business asked me what they could do to improve their search results. Because they were difficult to find when doing a search, they were concerned and wanted to do something to fix this problem.
Turns out, they weren’t listed in local search. If you have a local business, with the majority of your customers in your area, it’s important to be listed in local search, even if you also have a website and an Internet storefront.
To increase your visibility, customers need to be able to find you using search engines, starting with Google. Not only is it free, but it is quick to do.
Go to Google Places for Business, log in using your Google account or create a new one, and enter in the information for your business as prompted. Be sure to add photos and videos to give your business a more personal appeal.
3. No Social Networking
Online networking is an important component to your businesses online marketing. If you think it’s just a never-ending party with nothing work-related getting done, you’re misinformed.
When you build up your profile and build relationships on social media, you are also building traffic, which can lead to new connections and new customers. There is no cost to being active on social media outside of the time you invest, so decide on which networks you want to engage in and begin building a following.
By sharing content on social media, including the blog posts you write, you are creating another way for people to find you and share your content, opening the door to more traffic.
4. No Market Focus or USP
When marketing your product or service, find the problem and focus on the solution. Instead of focusing on the benefits alone, figure out how to solve your customer’s problem.
Spend time asking questions to determine what their problems are and how they can be solved. It’s easier to sell a solution to an existing problem than to sell a positive benefit.
As you go about the process of problem-spotting, be sure to keep your USP, unique selling proposition, in focus as well. As the one single statement that singles you out from your competition, it needs to be used in all of your online marketing.
5. No Data Measurement or Optimization
Online marketing gives you ample opportunity to measure data with analytics. Once you determine where your traffic is coming from, you can decide which sources are producing the most conversions.
Analytics tools will show you detailed performance data, giving you goal-setting information that you should continually update and change as necessary. If you discover there’s a particular source of traffic that’s giving you no leads, then eliminate it. Anything that’s giving you a lot of traffic or a high conversion rate, fine tune it for further improvements.
Data measurement and optimization is your roadmap to your online marketing efforts. Avoid the no’s of online marketing, stay on track, and don’t get lost by ignoring the results of your hard work.
Get Pay Per Click Advertising That Works

Pay per click advertising is like sending out a sales letter on the internet. Your intention is to get your audience to open the letter and make a targeted response. Instead of opening your letter, the goal of pay per click is to click on your ad.
You pay only when someone clicks on your ad, which then takes them to your website. To get your audience to click on your ad and follow through with a desired action, your pay per click advertising requires focus.
When you’re using pay per click advertising, it’s important to focus on more than just the number of clicks. A conversion happens when someone takes a desired action after they click on the ad. It could be making a purchase or registering to receive something free.
By staying focused on conversions, you can boost your returns while also increasing your subscriber rates. Follow these five ways to get pay per click advertising that works.
1. Build a Landing Page
When your audience clicks on your ad, don’t send them to your homepage. A targeted landing page with focused content and a specific call to action is the key to focusing on the keywords that brought your visitors to you and getting the conversions you want.
Depending on the type of keywords you are paying for, you might need to build more than one landing page. Just be sure to focus on the specific intent of your audience and what they are searching.
Don’t confuse your visitors by confusing them with irrelevant content. Stay focused on ad-related content that teaches your audience about what your product or service offers.
2. Make an Offer
Make the goal of your landing page more than selling your product or service. Your landing page is where your visitors go to receive your free offering, such as an ebook, audio recording, video presentation, or any type of informational resource.
This is the best way to differentiate yourself from your competition. With a compelling call to action such as “Free Download,” “Learn How,” or “Get Yours Free,” you will encourage your audience to act once they get to your landing page.
When you make an offer, you’re working to establish your relationship with the people who clicked. By building your subscriber list, you can continue to boost your conversion rates through your website and blog.
3. Use Negative Keywords
One of the underused yet effective pay per click strategies is to use negative keywords. By choosing keywords that won’t trigger your ad, you are essentially filtering out people who aren’t searching for your ad.
When you use negative keywords correctly, you will whittle down your clickers to only those who are interested in you and what you have to offer, saving you money in clicks. Negative keywords will control the relevancy of clicks without eliminating targeted traffic from broad keyword terms.
4. Location, Location, Location
Be sure to utilize the geo-location features of Google, Microsoft, and Yahoo search engines. This will allow you to target your market based on the IP addresses, focusing your campaign on regions, countries, cities, even zip codes.
Your pay per click advertising campaign might be to test out different locations in order to learn how different areas respond to what you sell. Or you might not ship to certain areas. Or you want to promote a special offer to only a specific region.
As brick and mortar store, you can use geo-location to not only drive traffic to your store, but to promote online sales to geo-targeted locations. It’s a good way to improve your performance in certain places by breaking out of your standard target zones.
5. Test for Results
Your pay per click advertising will give you better results when you test those results. Test multiple ads and gather the data to gauge their conversion rates.
Google AdWords will give you tools to analyze the metrics to determine where, when, and which ads show the highest conversion rates. Don’t just invest ad money and hope everything turns out for the best.
Your pay per click advertising can be a profitable tool to delivering your valuable content to an interested audience. An audience that clicks, signs up for your offer, and keeps on hearing from you through email newsletters, blog posts, and updates.
This is how pay per click advertising will work best – through your ongoing, focused efforts to stay connected.
Lynn A. Damon Photographic Artist
Why Email Marketing Is Still the Cat’s Meow

It’s so old school, why would anyone still use it? Hasn’t social media replaced it? Won’t people think you’re just spamming them?
These are valid questions and concerns about email marketing. These objections all hold a grain of truth, but they only apply to email marketing when it’s used incorrectly.
If you want to get results from your email newsletter, then be sure you’re doing a few things right.
Don’t Pussyfoot Around With Old-School Email
The cat is out of the proverbial bag. Yes, it’s the oldest internet marketing technology. But old-school email is also the new e-newsletter that grabs your readers attention with bright colors and compelling visuals.
Today’s email newsletter doesn’t have to look like it did a decade ago. With the aid of email marketing services such as Constant Contact, Mail Chimp, AWeber, and GetResponse, you can easily whip up a visual prey of delight in your email.
So when it comes to old-school email, don’t pussyfoot around thinking it’s no longer relevant. Commit yourself to a scheduled email newsletter as part of your marketing plan.
Who Needs Email When You Have Social Media?
Social media continues to be a great way to have conversations with your followers and customers. When you want to link to others, explore joint ventures, and meet people who share your interests, social media is the cool cat’s party.
Compare social media to an event where your objective is networking. It’s an ongoing, online event where you can build your name, where you can share your latest news. It’s the ideal platform for taking the information you send to your email recipients and sharing it with a wider audience.
What social media doesn’t do is make direct contact by landing in someone’s inbox. In other words, trying to position yourself as a leader to your social media followers can be like herding cats.
It’s one thing to be an authority on something, but to be a leader, you need to show you’re serious about what you do. The best way to do this is to deliver interesting content directly to the people who need it most.
Your email subscribers are like the audience of a radio talk show. According to Ben Settle, world class email specialist who delivers content to his subscribers daily, it’s the best way to keep a casual conversation going about what you have to offer your customers.
But Email Is So Spammy
The primary purpose of your email marketing is to sell your product or service. But that doesn’t mean your emails need to be spammy.
The essence of your email newsletters is to talk about your common interest or problem. Sometimes you won’t even mention your product in the email. You might just include a link to it.
Wherever it fits in naturally, within the context of the story you are telling in the email, find the right place to add information about what you can do to solve their problem. You are the invited guest in their inbox, and as their guest you are obligated to tell them how you can benefit them.
Always include a reference to how you can meet their need. Make this a clear call to action, and tell them what to click, where to go, or what to do next.
As your readers continue to receive your emails, the bonding process also continues. When they need what you are selling, you will be the one they turn to – the one they always hear from.
How Your Brand Can Stand Out With Visual Content
Social media makes it unavoidable: It’s important to engage in the conversation, or you’ll get lost in the crowd. By using a wide variety of imagery and visual techniques, you can represent your brand and get more attention and traffic.
All social media channels, even those that were more text-based, are now focusing on the visual component, thanks to what’s being called the Instagram Effect. Instagram is almost totally visual, relying on images to communicate its message.
Images have grown in size on Facebook, and videos now play automatically. Kissmetrics reports that Facebook “photos get 53% more likes, 104% more comments, and 84% more click-throughs on links than text-based posts.”
Even if you’re not a naturally visual business, such as a design or travel company, there are many ways to visualize the value of your brand, products, and services. There are visual opportunities for everyone to participate in the explosion of visual growth.
Here are four ways to create your visual content for social media:
Tell Stories With Images
When telling a story, think of a designated period of time and how to capture what’s happening. For example, it could be a product launch, a new building, a website makeover, a trade show or conference, a fundraising event, or the development of a prototype.
Whatever you choose to showcase, document it with a sequence of photos or videos. By chronicling the timeline of events, you’re sharing a behind-the-scenes peek and adding visual intrigue and engagement to ordinary processes.
Entertain With Memes
By creating memes – an image with simple accompanying text that represents an idea or makes a statement – you’re sharing your company’s personality. What better way to engage with followers than by highlighting your human side?
Use a quotation with striking typography and other graphic enhancements. Look for your quotes in relevant literature, popular culture, educational news, and even old advertisements.
Decades-old classic print ads from various advertising campaigns are great inspiration for your memes. Try Advertising Archives’ selection for inspiration to see how some brands managed to inspire and entertain without boasting or simply spewing out company slogans.
Information-Rich Infographics
The popularity of infographics is due to its concentration of valuable information that is formatted to tell a story. Having all that data compiled in one place is a visual feast for the data hungry.
Infographics can illustrate an abstract concept with humor, distinction, and imagination. With one post, you save your followers hours of gathering information on a specific topic.
Piktochart and Easelly are great places to start for do-it-yourself infographics. With ready-made templates and walk-through steps, you can turn your research into a customized visual story.
Online Presentations
Presentations continue to stand out as visually persuasive content. Thanks to the growing number of free online presentation tools, showcasing your own creativity and knowledge is easier than ever.
Besides the well-known Microsoft PowerPoint online, there is also Slideshare, Prezi, Haiku Deck, and Google Slides. With these tools, you can create a visual strategy that fuses art and copy to form a compelling presentation.
To get the best results, start your content creation so both your visual images and text work together to promote a unified concept. The end product should be more than just tacked-on graphics to your documents.
Reinvent the slideshow with a rich digital experience for your audience that’s easy to share across your social media platforms.
When sharing your visual creations, remember not to post every single image across all of your networks. Each social media platform has different image dimensions as well as unique community expectations. Make sure that your message is expressed in a format that reflects each platform’s identity.
For every visual you share, include something that will make your brand recognizable, such as a watermark or logo. By expressing your brand with visual creative planning, you will build trust and stand out from your competition.
Snapchat: What’s the Big Deal?

Remember having long conversations on telephones? Back when you had to pick up a landline, punch in a series of numbers, and then gab with your friends for hours?
That’s what Snapchat is for the Millennials – where today’s teens and young adults get their gab-fest fix. It’s no accident that they named it Snapchat.
The snap portion of its title corresponds to the ephemeral nature of the mobile app. Snapchat lets its users send pictures and videos that last only a few seconds. With a reported 100 million monthly users worldwide sending 700 million Snaps a day, it’s no wonder brands are interested.
Happily for any brand who wishes to communicate with the tech-savvy young generation, Snapchat said it’s now offering advertising. According to its blog post, the decision to begin ads is simple, they “need to make money.”
Any company looking to capitalize on this latest opportunity must adhere to one chief rule. It seems you can’t be “creepy and targeted.” Additionally, ads won’t be allowed in users’ personal communication, otherwise known as Snaps and Chats, because “that would be totally rude.”
Advertisers follow the same rules as users who post in Stories, the alternative way of sharing Snaps. They’re a series of Snaps added in the form of a narrative and are found in the “Recent Updates” section, disappearing after 24 hours or after they’re viewed.
The first advertisement appeared over the weekend and was far creepier than expected, given its no-creepy-ads-allowed rule. The Snap ad, a twenty second trailer to the horror movie Ouija, makes you wonder if their public advertising statement, “It’s going to feel a little weird,” was a cloaked warning from the dark beyond.
In case users are concerned about the new advertising gig, Snapchat assures us that you can choose whether or not you want to watch the Snap ad. It is, after all, “no biggie,” Snapchat explains.
So if it’s no biggie, then perhaps brands will no longer be reluctant to work with Snapchat despite the messaging app’s reputation as a potential conduit for disagreeable direct-response advertisers, teen sexting, and other inappropriate content.
Snapchat said they won’t be giving advertisers any user data and that it doesn’t wish to target its users. How Snapchat could manage to do this is unclear given the nature of the messaging service and the erasure of user information along with the messages.
Only the United States will be featuring this first run of advertisements, which means only the U.S. will be subject to advertising described by some as “untargeted spam.”
The creepy advertising comes at a time when 200,000 Snapchat images were leaked via an app that allows users to save Snapchats without the sender knowing. The app site, Snapsaved.com, has since closed down since what’s been called the “Snappening.”
Despite Snapchat’s recent brouhahas, brands should keep an eye on opportunities for promotions, including Snapchats of discounts and coupons. While about half of the users are between the ages of 13 and 17, 77% of college-aged students use Snapchat daily, with half of them saying “they would open a Snap from a brand they’d never heard of.”
If you’re not already Snapping (if that’s even a verb yet), then perhaps you ought to be.
Why the Password Will Never Die

A password is like a house key. It’s job is to secure the lock on your door. If you were to lose your key and a burglar got a hold of it and broke into your house, would it be the key’s fault?
The key is merely doing its other job of allowing entry. The blame rests on the burglar, or the fact that you managed to lose your key.
The same goes for passwords. Blaming passwords for security problems isn’t looking at the whole problem. How the hackers are able to steal vast amounts of data is the real issue.
When deciding how to protect users, it boils down to a choice between security and usability. Most of the time, the choice leans towards usability to make it easier for users. No one likes being locked out of their accounts.
Multi-Factor Authentication Gives You Better Security
More services, however, are adopting the option of a multi-factor authentication system as a heightened security measure. This system requires the combination of several things in order for access to be granted to your data.
Google, for example, has adopted a two-factor verification system which requires two things. One is something you have, in this case a verification code sent to your smartphone. It could also be a physical smart card or token you plug into your device. The second verification is something you know, such as your password or PIN.
A third possible verification for multiple factor authentication is something you are, like Apple’s iPhone option of using your fingerprint. Other possibilities include face, palm, or eye (retinal or iris) scanning.
Making the shift from service utilization to service security will give you greater data protection. Requiring users to adopt added layers of security will assure heightened security. Leaving users in charge of changing their behavior to create better and safer passwords, for example, is a doomed mission.
How Do Our Passwords Fail?
Passwords are guessed, recycled from password dump sites, cracked through brute force attacks, stolen with a remotely installed keylogger, or totally reset by a hacker.
Because guessing is the simplest method, it’s hard to believe that people continue to use predictable, shoddy passwords. There are free password-cracking tools that are available to anyone who wants to try and break in, often with helpful YouTube videos so any novice can do it.
Passwords are reused with wild abandon. You know you do it. You create the perfect combination of letters and numbers, and every time you need to devise a new password for a new account, you fall back on your handy password creation.
Thanks to the inundation of password “hashes,” encrypted but readily crackable passwords that are dumped online for anyone’s consumption, your reused password makes for easy entry into multiple accounts through a single point of failure.
The invention of the cloud makes the ability to trick customer service reps into resetting passwords easier than ever. A hacker can find all sorts of personal information about you online and then use that to gain entry, first into one account, then into another.
The password is not dead, but we need to change our terrible password habits. Strengthen your password and create different versions for different accounts. Use multi-factor verification whenever it is offered. Keep your password keys safe so they can do their job.
Do your part to save the password from death.
More Password Hacking Methods and How to Stay Safe
-

This work is a derivative of “Credit Card Theft” by Don Hankins, used under CC BY.
Nearly half of all adults had their personal information exposed by hackers this year. The total number of accounts compromised was 432 million. This ongoing targeted theft isn’t going away.
Last month, 5 million Gmail usernames and passwords were published on a Russian bitcoin security forum. This follows the 70 million Target customers’ personal information, 33 million Adobe user credentials, 4.6 million Snapchat users’ account data, 3 million Michael’s payment cards, and 1.1 million Neiman Marcus cards.
The damage is real. Each record typically includes personal information, such as your name, debit or credit card, email, phone number, birthday, password, security questions and physical address.
It’s enough to get hunted down by an abusive ex-spouse. It makes you an easier target for scams. And even if only basic information about you is stolen, that can easily be paired with stolen credit card data, empowering impostors.
Top-tier hackers continue to take advantage of the fact that we are increasingly moving our lives online. They will often publicize sensitive information for other hackers to scramble and use. Their exploits are multifarious, leaving its victims – and potential victims – to scramble to stay ahead of their game.
What You Can Do To Stay Safe
By staying aware of the methods hacker’s use and taking the appropriate steps to prevent attack, you will be far safer than other users. “Cybercriminals exploit the weakest target first.”(CSIS Security Group)
WiFi Sniffing
Anytime you’re in public using your phone, tablet, or laptop, and you’re connected to a network outside your home, you’re opening the door to WiFi sniffing.
While you are browsing through an unprotected WiFi, you’re also broadcasting your data to anyone who wants to look. Because your data is sent to the router on radio waves, it reaches all connected devices at the same time.
Most users won’t be paying attention to the data you send, but the fact is, someone could be using a WiFi sniffer to pick up the information you’re broadcasting. Your URLs, passwords, usernames, and any other private data is up for grabs.
Use a VPN service which provides encryption in its connection. A virtual private network extends your private network across the public network, giving your WiFi-enabled device the same security it has when on your private network.
Malware Attacks
Malware are hidden programs that bury inside of your computer and then send data to other people without your knowledge. They are an epidemic on Windows and Android programs.
The most common method is through installing a keylogger or another type of spyware in your computer that watches what you type on the keyboard or see on the screen. In many cases, the goal is to steal entire systems of passwords and data, so the targets are often large organizations.
A devastating malware example is Zeus, a Trojan horse virus which made its appearance in 2007. This example combined the tactics of phishing with email to send users a rogue link. Once clicked on, the malware is installed in your computer and waits for you to log in to your online banking account.
In the case of Zeus, small businesses were a prime target, with $70 million stolen from 390 victims in one case in 2010. Educate yourself and employees on phishing email and link-clicking only on trusted sites and sources.
Security Questions
Hackers who gain access to your email account will often have an easy time of cracking your security questions. Because they have access to your social media, deducing the answers to basic security questions like “What city were you born in?” or even “What’s your favorite pet’s name?” is a walk in the park,
Once they manage to break through this flimsy security barrier, they are able to reset your password and get into your accounts. When you answer security questions, it’s a good idea to either answer with a lie or choose “other” when offered and create a security question that’s impossible for someone to guess.
Cyber Security Threats: Is This the Digital Wild West?

The battle is on and you’re a potential target. It doesn’t matter what you do to protect yourself from data theft, it is a real possibility.
Like a bank robbery, cyber threats will always be a present danger. As technology continues to advance, new methods of thievery are being devised.
You can, however, try to stay out of the crossfire. Keeping aware of the different password hacking methods used to steal your data is the first step in tightening your own security measures.
How Safe Are You from Password Hacking?
The most common form of hacking involves password and username theft. Our online passwords fail in every imaginable way when it comes to cyber security.
There are a variety of strategies hackers use to break into your accounts and steal your password. These three common methods are the first in the line of fire on your security.
Password Scavenging/Recycling
Most hackers rely on other more adept cyber criminals to grab your password and username. Scavenging takes place when the top-level hackers put stolen passwords hacked by compromising a database into a temporary public document for others to grab and use.
Once these hackers have their hands on your information, they try your password out on known services like PayPal. Imagine the fun they have when they discover that these users have the same password across many different accounts!
Phishing
Most of us have been recipients of attempted phishing because we have an email account. Hackers try to get your password and username (as well as your money) by pretending to be a website or company you trust.
The email will appear to be valid and authentic. Last week I received one from Delta airlines saying my ticket was attached and ready for printing. Funny thing is, I don’t recall planning on traveling to Oakland, CA!
Sometimes the emails are from your friends, but they normally will contain little information except the infected link.
Cloud Breaching
There’s a new school of hacking that’s rivaling phishing. This new wave of password theft involves breaching the cloud where vast amounts of data lie. If you weren’t already nervous about password theft, this new development is worth your attention.
Thanks to the recent news of the celebrity photo iCloud breach, more people are learning about this vulnerability. In the case of the celebrities, Apple said in a statement that certain celebrity accounts were compromised by “a very targeted attack on user names, passwords and security questions.”
Because we tend to reuse our passwords and usernames in multiple accounts, your personal information stored in the cloud is ripe for exploitation as one service allows entry into another. Tricking customer service agents into resetting passwords is a growing complication to this devastating method.
Stay tuned for more password hacking methods next week, followed by what you can do to protect yourself. Even the Wild West was eventually tamed.
- « Previous Page
- 1
- …
- 15
- 16
- 17
- 18
- 19
- …
- 46
- Next Page »