WordPress 3.9 Is Named After a Jazz Pioneer
The new WordPress 3.9 features will make your life rock, or rather jazz, since the memorial naming of new versions is after jazz musician greats. Jimmy Smith, whose organ-loving skills brought said instrument into the jazz and blues music scene, is the namesake for the latest version.
Only two of the twenty-four WordPress versions have been named after female jazz greats: Ella Fitzgerald and Carman McRae. Seeing how code lacks any biological characteristics, you could argue that it’s irrelevant whether a version has a male or female name.
But still.
The latest “Smith” WordPress 3.9 version has a great roundup of new features. Even if it is another male moniker. Here’s how it works.
Audio Video Playlists
There’s no need to install a plugin to create your own playlist of songs. You upload video and audio using the media library, just like you do images. Once added, you can choose to create a playlist.
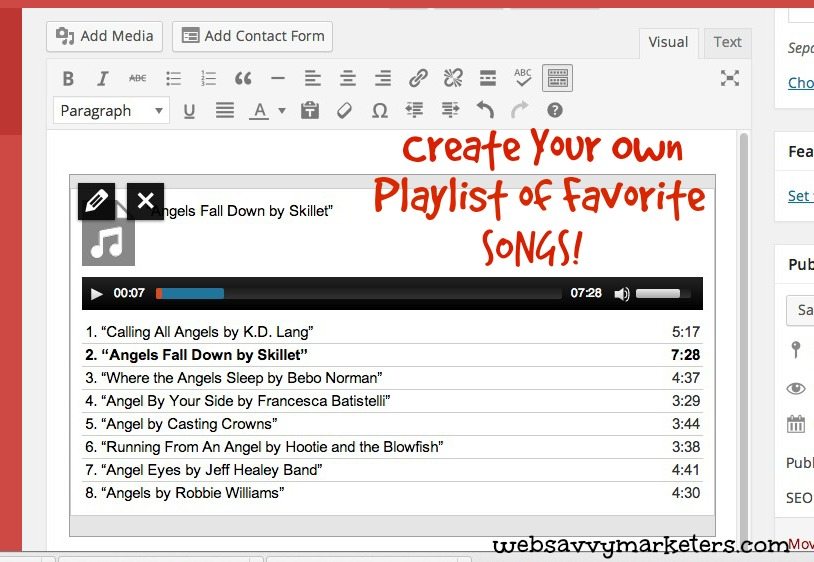 Just drag and drop your favorite tunes right from iTunes! The album cover artwork is supposed to be added, but it doesn’t seem to work consistently. If it does fetch the artwork, it will display for the tune selected for play in the post.
Just drag and drop your favorite tunes right from iTunes! The album cover artwork is supposed to be added, but it doesn’t seem to work consistently. If it does fetch the artwork, it will display for the tune selected for play in the post.
Mad Media Gallery
No more navigating back and forth between the edit page and the media library. Now you can see live previews of your media, including a new media gallery view.
The updated visual editor also allows you to drag and drop your images from your desktop right into your post. When you do this, the images are automatically added to the media library and formatted to the post.
Instant Image Resizing
Once your image is added to your edit page, you can also resize it right on the page.
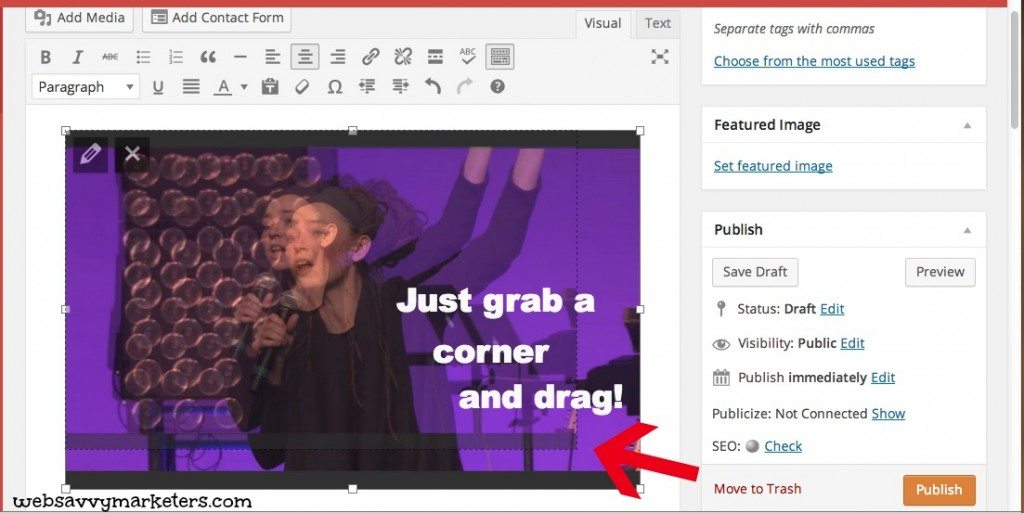 Forget the days of having to open and reopen the edit window to make incremental reductions in size. All you have to do is click on the image, grab the corner, and drag.
Forget the days of having to open and reopen the edit window to make incremental reductions in size. All you have to do is click on the image, grab the corner, and drag.
Wonderful Widgets
Widgets are easier than ever to add and view. Without having to leave the screen for a preview, and then refreshing it to see how it looks, you can see an immediate view of them in the sidebar.
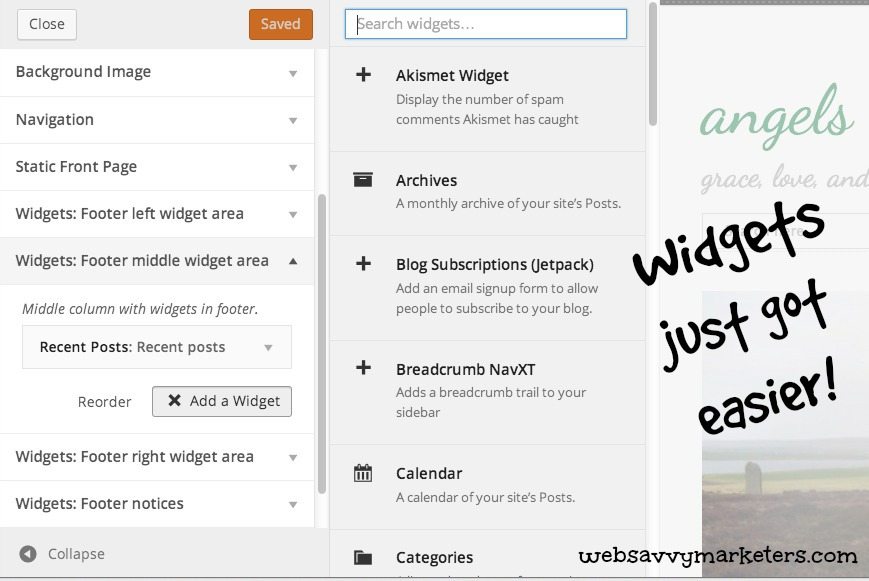 All this is done from the theme customizer. Once you’re satisified with your changes, then you can save them for the rest of the world to see.
All this is done from the theme customizer. Once you’re satisified with your changes, then you can save them for the rest of the world to see.
No-Fuss Copy and Paste
This added feature lets you copy your Word-type document and paste into your edit page without all those annoying added paragraph breaks.
You are free to end your backspacing antics in order to rid your text of all the paragraph gaps. Things transition smoothly, unless you’re copying and pasting from Google Drive. No such luck with pasting from that software – you’re still going to be deleting paragraph breaks.
Easy Theme Preview and Installs
Want to try a new theme? Now it’s easier than ever to browse and try out new ones. The header image feature is also improved for more flexible image additions and changes.
Now that you know how it works, update to WordPress 3.9 and start having some fun!